What is bot mitigation?
Bot mitigation is the reduction of risk to applications, APIs, and backend services from malicious bot traffic that fuels common automated attacks such as DDoS campaigns and vulnerability probing.
Bot mitigation is the reduction of risk to applications, APIs, and backend services from malicious bot traffic that fuels common automated attacks such as DDoS campaigns and vulnerability probing.
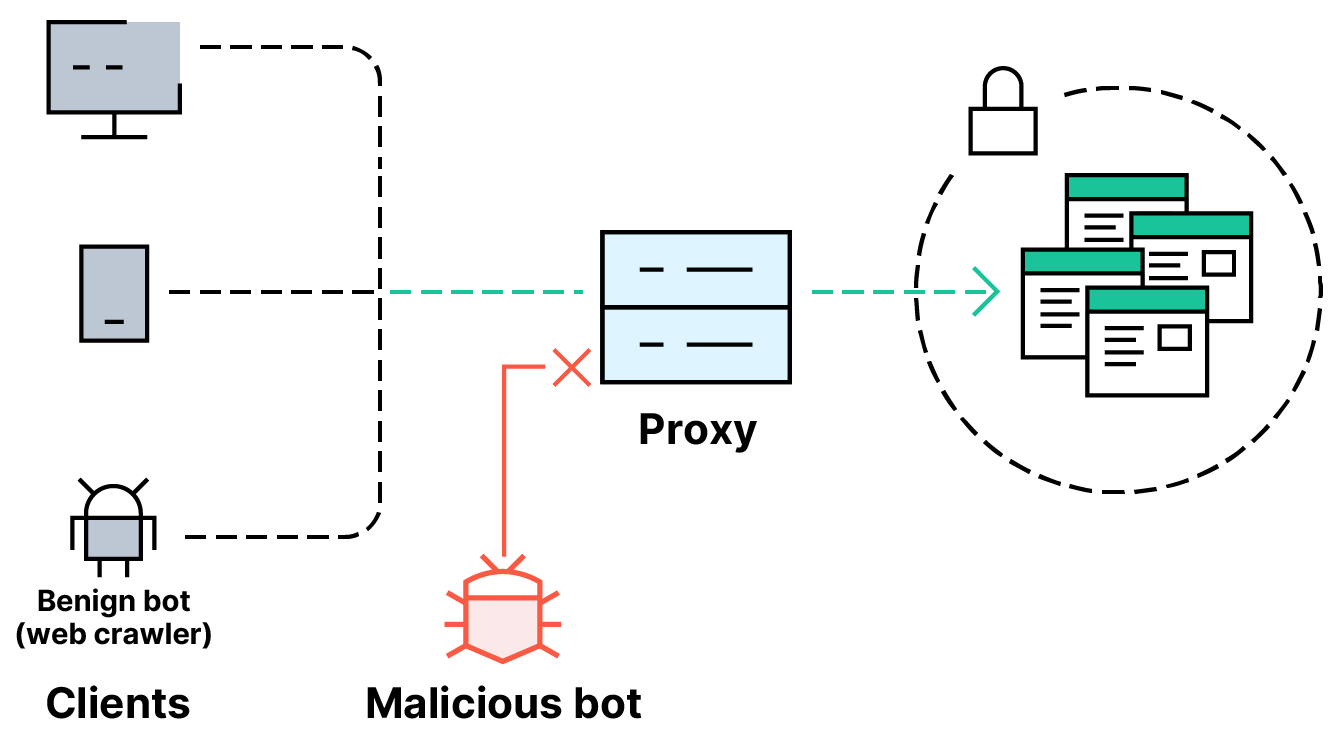
Bot mitigation solutions leverage multiple bot detection techniques to identify and block bad bots, allow good bots to operate as intended, and prevent corporate networks from being overwhelmed by unwanted bot traffic.
The solution
A growing share of all internet traffic is driven by advanced bots — software applications that use automation to perform tasks. These bots can do anything from filling out a web form to conducting a real-time conversation with a human, but may also be used maliciously to carry out a Layer 4-7 distributed denial-of-service (DDoS) attack against an online business, overwhelm a key API, or continuously check a site for cross-scripting (XSS) vulnerabilities. Overall, bot attacks are a growing cause of data breaches and financial losses.
Reliably thwarting bot and botnet attacks requires a bot mitigation platform that can:
Companies such as airlines and financial services providers are some of the most common targets of bot attacks. However, organizations of all types are increasingly exposed to the risks of malicious bots attempting to inundate networks — and they need reliable bot mitigation solutions for better fraud protection, as well as improved API and application security.
A bot mitigation solution may employ multiple types of bot detection and management techniques. For more sophisticated attacks, it may leverage artificial intelligence and machine learning for continuous adaptability as bots and attacks evolve. For the most comprehensive protection, a layered approach combines a bot management solution with security tools like web application firewalls (WAF) and API gateways through. These include:
IP address blocking and IP reputation analysis: Bot mitigation solutions may maintain a collection of known malicious IP addresses that are known to be bots. These addresses may be fixed or updated dynamically, with new risky domains added as IP reputations evolve. Dangerous bot traffic can then be blocked.
Allow lists and block lists: Allow lists and block lists for bots can be defined by IP addresses, subnets and policy expressions that represent acceptable and unacceptable bot origins. A bot included on an allow list can bypass other bot detection measures, while one that isn’t listed there may be subsequently checked against a block list or subjected to rate limiting and transactions per second (TPS) monitoring.
Rate limiting and TPS: Bot traffic from an unknown bot can be throttled (rate limited) by a bot management solution. This way, a single client can’t send unlimited requests to an API and in turn bog down the network. Similarly, TPS sets a defined time interval for bot traffic requests and can shut down bots if their total number of requests or the percentage increase in requests violate the baseline.
Bot signature management and device fingerprinting: A bot signature is an identifier of a bot, based on particular attributes such as patterns in its HTTP requests. Likewise, device fingerprinting reveals if a bot is linked to certain browser attributes or request headers associated with bad bot traffic.
NetScaler's advanced bot mitigation capabilities provide robust protection for your applications and APIs. Bot mitigation works in tandem with NetScaler WAF and DDoS protections to ensure comprehensive security across your monolithic and microservices-based applications.
Request a demo or talk to sales
1-866-NetScaler